Difference between revisions of "Security"
(→How to harden your system) |
(→Introduction) |
||
| (11 intermediate revisions by 2 users not shown) | |||
| Line 4: | Line 4: | ||
|} | |} | ||
| − | |||
==Introduction== | ==Introduction== | ||
On this page we will collect information to harden your system. | On this page we will collect information to harden your system. | ||
| + | To check your security you can use [https://opensource.com/article/20/5/linux-security-lynis Lynis security scan]. | ||
| + | |||
| + | '''Firstly''', install [https://svnweb.freebsd.org/ports/head/security/lynis/pkg-descr?revision=HEAD lynis]:<br/> | ||
| + | |||
| + | <code>sudo pkg install lynis</code> | ||
| + | |||
| + | |||
| + | '''Secondly''', conduct an audit:<br/> | ||
| + | |||
| + | <code>sudo lynis audit system</code> | ||
| + | |||
| + | |||
| + | Hardening your system to receive a better Hardened Index score is trivial. | ||
==How to harden your system== | ==How to harden your system== | ||
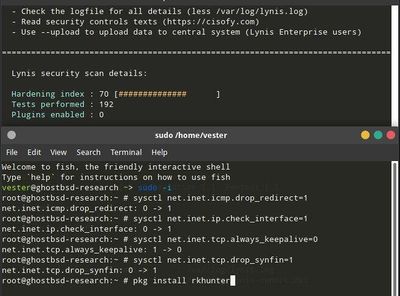
| − | + | To have GhostBSD score a 70 on the audit. Install [http://rkhunter.sourceforge.net/ rkhunter] and change 4 settings. | |
[[File:Photo 2020-11-08 12-40-56.jpg|400px]] | [[File:Photo 2020-11-08 12-40-56.jpg|400px]] | ||
| Line 18: | Line 30: | ||
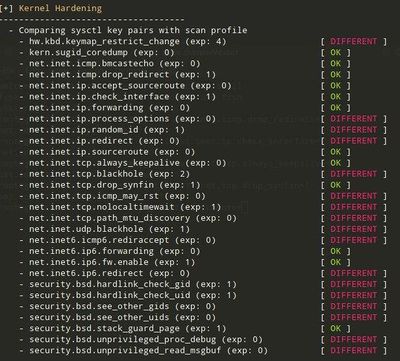
You can make additional changes to improve the score. Feel free to test to see what is comfortable for you. | You can make additional changes to improve the score. Feel free to test to see what is comfortable for you. | ||
| − | + | [[File:Photo 2020-11-08 12-44-00.jpg|400px]] | |
| + | |||
If we simply set the network related values, we will not affect the user experience. | If we simply set the network related values, we will not affect the user experience. | ||
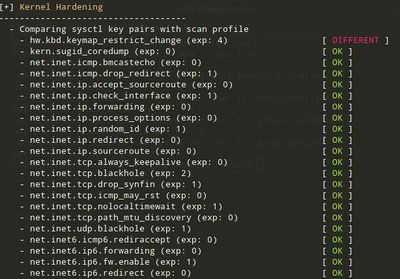
| − | + | [[File:Photo 2020-11-08 12-57-52.jpg|400px]] | |
| + | |||
| + | These changes plus adding one pkg (rkhunter) will provide a score of 77. | ||
| + | |||
| + | |||
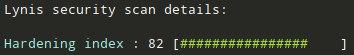
| + | However, it is possible to attain a score of 82 by enabling several additional security.bsd settings. | ||
| + | |||
| + | [[File:Photo 2020-11-08 13-13-23.jpg|400px]] | ||
| − | + | For those that want to have these changes be persistent after reboot, add them to '''/etc/sysctl.conf'''. | |
| − | + | Also, if you do not want to use rkhunter, it is possible to replace it with [https://www.clamav.net/ clamav]. | |
| + | Both rkhunter and clamav help to raise the hardened index score. | ||
| + | ==How could keep those change - How setting security== | ||
| − | + | Append /etc/sysctl.conf with these entries: | |
| − | + | hw.kbd.keymap_restrict_change=4 | |
| + | kern.sugid_coredump=0 | ||
| + | net.inet.icmp.bmcastecho=0 | ||
| + | net.inet.icmp.drop_redirect=1 | ||
| + | net.inet.ip.accept_sourceroute=0 | ||
| + | net.inet.ip.check_interface=1 | ||
| + | net.inet.ip.forwarding=0 | ||
| + | net.inet.ip.process_options=0 | ||
| + | net.inet.ip.random_id=1 | ||
| + | net.inet.ip.redirect=0 | ||
| + | net.inet.ip.sourceroute=0 | ||
| + | net.inet.tcp.always_keepalive=0 | ||
| + | net.inet.tcp.blackhole=2 | ||
| + | net.inet.tcp.drop_synfin=1 | ||
| + | net.inet.tcp.icmp_may_rst=0 | ||
| + | net.inet.tcp.nolocaltimewait=1 | ||
| + | net.inet.tcp.path_mtu_discovery=0 | ||
| + | net.inet.udp.blackhole=1 | ||
| + | net.inet6.icmp6.rediraccept=0 | ||
| + | net.inet6.ip6.forwarding=0 | ||
| + | net.inet6.ip6.fw.enable=1 | ||
| + | net.inet6.ip6.redirect=0 | ||
| + | # The settings below will change the user experience | ||
| + | security.bsd.hardlink_check_gid=1 | ||
| + | security.bsd.hardlink_check_uid=1 | ||
| + | security.bsd.see_other_gids=0 | ||
| + | security.bsd.see_other_uids=0 | ||
| + | security.bsd.stack_guard_page=1 | ||
| + | security.bsd.unprivileged_proc_debug=0 | ||
| + | security.bsd.unprivileged_read_msgbuf=0 | ||
==Additional Information== | ==Additional Information== | ||
Latest revision as of 15:39, 8 November 2020
| Welcome to the |
Contents
[hide]Introduction[edit]
On this page we will collect information to harden your system.
To check your security you can use Lynis security scan.
Firstly, install lynis:
sudo pkg install lynis
Secondly, conduct an audit:
sudo lynis audit system
Hardening your system to receive a better Hardened Index score is trivial.
How to harden your system[edit]
To have GhostBSD score a 70 on the audit. Install rkhunter and change 4 settings.
You can make additional changes to improve the score. Feel free to test to see what is comfortable for you.
If we simply set the network related values, we will not affect the user experience.
These changes plus adding one pkg (rkhunter) will provide a score of 77.
However, it is possible to attain a score of 82 by enabling several additional security.bsd settings.
For those that want to have these changes be persistent after reboot, add them to /etc/sysctl.conf.
Also, if you do not want to use rkhunter, it is possible to replace it with clamav. Both rkhunter and clamav help to raise the hardened index score.
How could keep those change - How setting security[edit]
Append /etc/sysctl.conf with these entries:
hw.kbd.keymap_restrict_change=4 kern.sugid_coredump=0 net.inet.icmp.bmcastecho=0 net.inet.icmp.drop_redirect=1 net.inet.ip.accept_sourceroute=0 net.inet.ip.check_interface=1 net.inet.ip.forwarding=0 net.inet.ip.process_options=0 net.inet.ip.random_id=1 net.inet.ip.redirect=0 net.inet.ip.sourceroute=0 net.inet.tcp.always_keepalive=0 net.inet.tcp.blackhole=2 net.inet.tcp.drop_synfin=1 net.inet.tcp.icmp_may_rst=0 net.inet.tcp.nolocaltimewait=1 net.inet.tcp.path_mtu_discovery=0 net.inet.udp.blackhole=1 net.inet6.icmp6.rediraccept=0 net.inet6.ip6.forwarding=0 net.inet6.ip6.fw.enable=1 net.inet6.ip6.redirect=0 # The settings below will change the user experience security.bsd.hardlink_check_gid=1 security.bsd.hardlink_check_uid=1 security.bsd.see_other_gids=0 security.bsd.see_other_uids=0 security.bsd.stack_guard_page=1 security.bsd.unprivileged_proc_debug=0 security.bsd.unprivileged_read_msgbuf=0
Additional Information[edit]
| Back to the |